Dateline: September 4, 2015
Welcome to our Friday WRAP – one thought-provoking idea to think about over the weekend.
Let’s talk IT security. It’s probably one of the least favorite topics for IT leaders, but of course one of the most crucial since protecting assets is critical for business success. Recently I ran across a well-written white paper published by Dell’s SecureWorks titled, “The Path Ahead for Security Leaders“. They describe the basic process for threat actors.
The Kill Chain is a documented methodology that explains a threat actor’s process. Learning this process—even though each incident will have variables—enables security leaders to take a strategic approach to defend, resist, and respond to disrupt the threat actor’s progress toward acting on their objectives. Finally, the threat actor must be eradicated from your environment.
The Kill Chain is nicely articulated in this figure. The black arrow is the threat actor’s process and the colorful overlays are the security team responses.
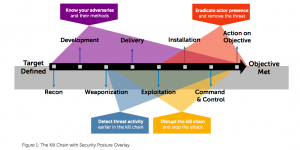
Source: http://www.secureworks.com/assets/pdf-store/white-papers/White-Paper-Path-Ahead-for-Security-Leaders.pdf
Do you know who your threat actors are? What is your information security plan to deflect/defend against them?
That’s a WRAP! Have a great weekend!
Speak Your Mind